UPDATE: Anonymous in comments
says to go here to find out what to do if the worm has infected your Twitter account - the info looks pretty good. The comment also says that the domain uuuq.net was hosted at Zymic.com, not GoDaddy.
UPDATE:
Twitter user jay_neff has
done some research on Mikeyy Mooney and found out he appears to be from from Winnfield, LouisianaUPDATE: I have made mistakes about who is hosting the servers. This is because I thought the companies that rented the domain names - apparently GoDaddy and Dreamhost - were the same ones renting the server space. See further corrections below and in the comments.
A 17 year old embryo scammer/spammer calling himself "Mikeyy [sic] Mooney", who says he is the founder of
Twitter rip-off stalkdaily.com,
has admitted launching a worm that has hijacked people's Twitter accounts today.
UPDATE: before admitting to being behind the worm, "Mikeyy" LIED to people on his own stalkdaily.com site asking him about the twitter hijacking - see Screenshot 5 below for the evidence of this, or check the account "mikeyy" on stalkdaily.com - No, I'm not linking to it!
A
full account of the worm is available here at the Mashable site. The worm has deliberately changed the web link in people's Twitter profiles to point to "Mikeyy"'s own rip-off site, and has
also hijacked people's twitter accounts and sent spam messages from them, promoting himself. If you notice an account that is sending messages about "Mikeyy", DO NOT CLICK ON IT!!!! Your account will be hijacked too. Twitter will no doubt let us know when all is safe again.
I did a
whois lookup to see who owns the stalkdaily.com account. There is no personal info available, unfortunately, but the whois search reveals that the stalkdaily.com site is hosted by Dreamhost.
UPDATE/CORRECTION: The stalkdaily site is
hosted by FastServers, NOT Dreamhost. FastServers' abuse reporting address is
abuse@fastservers.comI have sent a similar email to the one I sent to Dreamhost to FastServers - please consider sending one yourself. CORRECTION ENDS.
So I have sent an email to
abuse@dreamhost.com asking them to cancel this loser's accounts:
Dear Madam, or Sir,
I am writing to let you know that a website hosted by you - according to a whois lookup - admits responsibility for launching a worm that has exploited security holes in the Twitter.com website, of which I am a member. The worm has been hijacking accounts and sending spam updates from those accounts, which has directly impacted my enjoyment and use of the twitter.com site. I attach a screenshot of the Twitter Search site, showing these spam messages.
The website is www.stalkdaily.com
I attach a screenshot of the front page of www.stalkdaily.com where the purported owner of the site - or someone with permission to post to that site's front page - admits that they are responsible for creating the worm. The article the link on the front page leads to is at http://www.bnonews.com/news/242.html
Since the worm links people's Twitter accounts to stalkdaily without their knowledge or consent, I can only assume that this is a breach of your terms of service.
I would appreciate it if you would delete all accounts held by this account holder immediately.
If you want to get this moron punished, please do the same - send a complaint email to
abuse@dreamhost.com asking them to cancel "Mikeyy"'s accounts. Let's get this fool kicked off the Internet, if only for a while.
If your acccount has been infected, this link will tell you what to do:
http://mashable.com/2009/04/11/stalkdaily-twitter/?disqus_reply=8093439#comment-8093287UPDATE:
This blog post seems to show that the actual domain where the malicious script was hosted is uuuq.com. A whois lookup of that domain name
indicates it is hosted by GoDaddy. [UPDATE: A comment and
the page it says to look at indicates that the script was hosted at zymic.com]
I
have used this page to submit an email to GoDaddy as well:
Dear Madam, or Sir,
I am writing to you about the Twitter worm active today, April 12 2009, that was apparently hosted at a domain name that GoDaddy hosts.
Details of the worm can be found here: http://mashable.com/2009/04/11/stalkdaily-twitter/
This blog post: http://dcortesi.com/2009/04/11/twitter-stalkdaily-worm-postmortem/
indicates that malicious script that was used to hack the Twitter website, affecting my user experience there, was hosted at uuuq.com. A whois lookup: http://reports.internic.net/cgi/whois?whois_nic=uuuq.com&type=domain
indicates that GoDaddy is the host of this domain.
I assume that hosting malicious scripts on your servers is a breach of your Terms of Service. I ask that you delete all accounts hosted by the owner of uuuq.com
Regards,
David Jackmanson
UPDATE:
This post at the Mundoreves blog says the new attack on Twitter is by a script hosted at ireel.com. The Whois lookup for ireel.com indicates it is hosted by Ideal Media in Quebec, email address
- yes, a HOTMAIL address, which makes the company sound pretty fly-by-night AT BEST.
So I've sent another email off:
Dear Madam, or Sir,
I am writing because of this blog post: http://www.mundoreves.com/display/HOME/2009/04/12/Examining+the+StalkDaily-Mikeyy+twitter+worm... , which indicates that malicious script has been hosted on your site that has been used to hack the Twitter.com site, which has affected the experience of many users, including myself.
I would appreciate it if you could check this, and if it is indeed the case, if you would stop anyone hosting this sort of malicious script on your servers.
Regards,
David Jackmanson
Screenshot 6 below shows the whois lookup that provided me with this information.
Click on the screenshots below to see full-sized versions of them.
Screenshot 1: Stalkdaily.com's "Mikeyy" admits he is behind the worm:

Screenshot 2: Twitter Search shows how "Mikeyy" has infested the Twitter timeline:
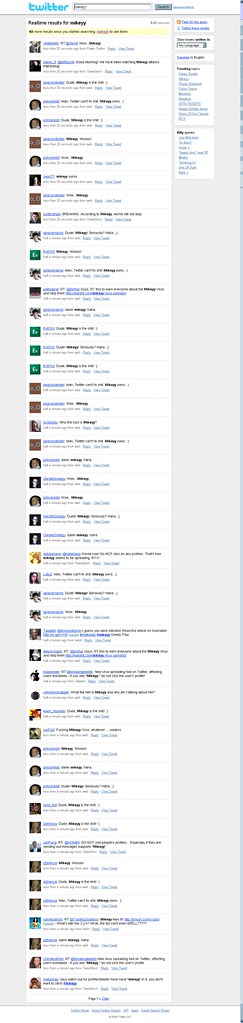
Screenshot 3: Whois lookup screenshot confirming that stalkdaily.com is hosted by Dreamhost:

Screenshot 4: Whois lookup screenshot confirming that uuuq.com - host of the malicious script - is hosted by GoDaddy.com

Screenshot 5: Evidence that "Mikeyy" LIED to members of his own stalkdaily.com site about his involvement in the Twitter hijacking:

Screenshot 6: Whois lookup for ireel.com

Read More...
Summary only...











